- hacker
- description
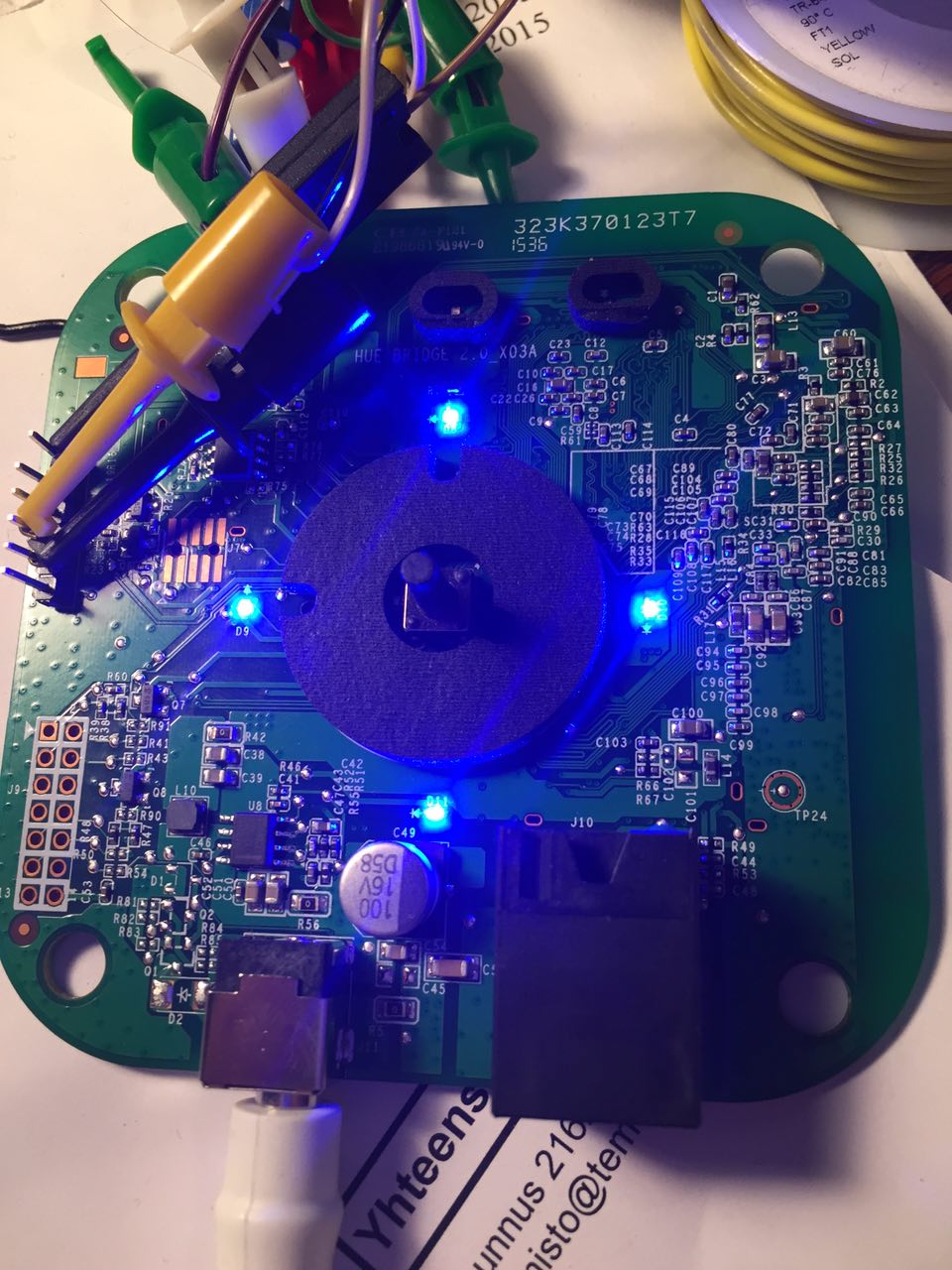
- I will try to get shell from the PHILIPS hue bridge v 2.0. You can find my raw notes from here
- started
2015-12-29
https://www.reddit.com/r/Hue/comments/3x12y6/jailbreaking_the_v2_hub/
Get shell with HW hacking: https://forum.openwrt.org/viewtopic.php?id=66346
http://colinoflynn.com/2016/07/getting-root-on-philips-hue-bridge-2-0/
Contents
Getting root shell (HW hacking)
Gudos for Colin O’Flynn and pepe2k for figuring out how to intercept the u-boot process and get access to u-boot console. I followed their instructions and managed to pull it through.
Check their instructions:
I did the following:
- Soldered pins for serial port
- Used the trick provided by Colin o Flynn
- Changed bootdelay to 3
Changed the security environmental to my own hash.
ath> setenv security '$5$wbgtEC1iF$ugIfQUoE7SNg4mplDI/7xdfLC7jXoMAkupeMsm10hY9' ath> setenv bootdelay 3 ath> savenev ath> reset
- After first boot and login:
Add your SSH public key to ''/etc/droppear/authorized_keys''
# iptables -I input_lan_rule -p tcp --dport 22 --syn -j ACCEPT
or if you want to do permanent change add folowing to: /etc/config/firewall
config rule 'ssh'
option name Allow-ssh
option src lan
option proto tcp
option dest_port 22
option target ACCEPT
option family ipv4
After that you can use SSH
WiFi / WLAN
- There is WLAN chip
- There is Wireless configuration in /etc/config/wireless (wlan disabled)
... # REMOVE THIS LINE TO ENABLE WIFI: option disabled 1
- After removing you have active wlan0 -device
- However there is no antenna
- There seems to be jack for antenna if you want to hack your own
u-boot env
ath> printenv
# Standard configuration
baudrate=115200
ethaddr=0x00:0xaa:0xbb:0xcc:0xdd:0xee
# Factory IP config environment
# Factory programming helpers
board=bsb002
flasht=tftp 0x80060000 ${board}/${board}_uboot.bin&&erase 0x9f000000 +$filesize&&cp.b $fileaddr
0x9f000000 $ize
flash_uboot_env=tftp 0x80060000 ${board}/${board}_uboot_environment.bin&&erase 0x9f040000 +$fil
esip.b $fileaddr 0x9f040000 $filesize
flash_uboot_and_env=tftp 0x80060000 ${board}/${board}_uboot_and_enment.bin&&erase 0x9f000000 +$filesize&&cp.b $fileaddr 0x9f000000 $filesize
flash_art=tftp 0x80060000 $d}/${board}_art.bin&&erase 0x9f070000 +$filesize&&cp.b $fileaddr 0x9f070000 $filesize
flash_kernel_0=t0x80060000 ${board}/kernel.bin&&nand erase 0x0 0x400000&&nand write $fileaddr 0x0 esize
flash_root_0=tftp 0x80060000 ${board}/root.bin&&nand erase 0x400000 0x28000and write $fileaddr 0x400000 $filesize
flash_kernel_1=tftp 0x80060000 ${board}/kernel.bin&&nand erase 0000 0x400000&&nand write $fileaddr 0x2C00000 $filesize
flash_root_1=tftp 0x80060000 ${board}/root.binnd erase 0x3000000 0x2800000&&nand write $fileaddr 0x3000000 $filesize
flash_overftp 0x80060000 ${board}/overlay.bin&&nand erase 0x5800000 0x2800000&&nand write $fileaddr 0x5800000 $fize
flash_factory=run flash_uboot_and_env&&run flash_kernel_0&&run flash_root_0&&rash_overlay
# Boot configuration - common
std_bootargs=board=BSB002 console=ttyS0,115200 ubi.mtd=overootfs=/dev/mtdblock:rootfs rootfstype=squashfs noinitrd init=/sbin/init
# Boot configuration - slot 0parts0=spi0.0:256k(u-boot)ro,128k(u-boot-env),64k(reserved),64k(art);spi0.1:4m(kernel-0)ro,40m(root-0),rnel-1),40m(root-1),-(overlay)
kernel_0_start=0x0
boot_from_slot_0=setenv bootargs ubi.mtd=5 ${std_bgs} mtdparts=${mtdparts0}; nboot 0x81000000 0 ${kernel_0_start}
# Boot configuration - slot 1
mtdparti0.0:256k(u-boot)ro,128k(u-boot-env),64k(reserved),64k(art);spi0.1:4m(kernel-0),40m(root-0),4m(kernel-10m(root-1),-(overlay)
kernel_1_start=0x2C00000
boot_from_slot_1=setenv bootargs ubi.mtd=7 ${std_bootamtdparts=${mtdparts1}; nboot 0x81000000 0 ${kernel_1_start}
# Boot command
# Selected slot
ethact=eeui64=001788fffe2179c6
set12nc=HueBridge2K15
ctn=HueBridge2K15
portal=9e345a8da10e5b5290beeed85edb00ecurity=$5$BkwEJP3Tp/u8Q2Za$qQXbcKEibHVPel.8.GXb8ds46DG29yFyeFZa6JKF7o2
homekit=028-08-483
hwrevision
production=1537
ipaddr=192.168.11.179
serverip=192.168.11.66
bootcmd=if test ${bootslot} -ne 1;the boot_from_slot_0;else run boot_from_slot_1;fi
bootdelay=0
frcnt=4
bootslot=1
stdin=serial
stdoutal
stderr=serial
bootargs=ubi.mtd=7 board=BSB002 console=ttyS0,115200 ubi.mtd=overlay rootfs=/dev/mtd:rootfs rootfstype=squashfs noinitrd init=/sbin/init mtdparts=spi0.0:256k(u-boot)ro,128k(u-boot-env),6served),64k(art);spi0.1:4m(kernel-0),40m(root-0),4m(kernel-1)ro,40m(root-1),-(overlay)
ath> printenv security
security=$5$BkwEJP3Tp/u8Q2Za$qQXbcKEibHVPel.8.GXb8ds46DG29yFyeFZa6JKF7o2
Geric Info
Serial port
You can find serial port/UART from the board (Details later)
Boot messages
[ 0.000000] Movable start for each node
[ 0.000000] Early memory node ranges
[ 0.000000] node 0: [mem 0x00000x03ffffff]
[ 0.000000] Primary instruction cache 64kB, VIPT, 4-way, linesize 32 bytes.
[ 0.000000] Primary data cache 32kB, 4-way, VIPT, cache aliases, linesize 32 bytes
[ 0.000000] Built 1 zonelists in Zone order, mobility grouping on. Total pages: 1
[ 0.000000] Kernel command line: ubi.mtd=5 board=BSB002 console=ttyS0,115200 ubi.mtd=overlay rootev/mtdblock:rootfs rootfstype=squashfs noinitrd init=/sbin/init mtdparts=s
pi0.0:256k(u-boot)ro,128k(u-env),64k(reserved),64k(art);spi0.1:4m(kernel-0)ro,40m(root-0),4m(kernel-1),40m(root-1),-(overlay) mem=ootfstype=squashfs,jffs2 noinitrd
[ 0.000000] PID hash table entries: 256 (order: -2, 1024 bytes)
[ 0.000000] Dentry cache hash table entries: 819der: 3, 32768 bytes)
[ 0.000000] Inode-cache hash table entries: 4096 (order: 2, 16384 bytes)
[ 0.000000] Writing ErrCtl register=00000000
[ 0.000000] Readback ErrCtl register=0000
[ 0.000000] Memory: 60756K/65536K available (2712K kernel code, 126K rwdata, 576K rodata, 160K init, 185K bss, 4780K reserved)
[ 0.000000] SLUB: HWalign=32, Order=0inObjects=0, CPUs=1, Nodes=1
[ 0.000000] NR_IRQS:51
[ 0.000000] Clocks: CPU:650.000MHz, DDR:597.583MHz, AHB:216.666MHz, Ref:25.000MHz
[.000000] Calibrating delay loop... 432.53 BogoMIPS (lpj=2162688)In details: /BootMessage
Bootlog with full debug (enabled with hitting "4" and <enter>: /BootMessageWithFullDebug
Update with full debug: /UpdateWithFullDebug
Login
I did press "f" and enter.
Press the [f] key and hit [enter] to enter failsafe mode Press the [1], [2], [3] or [4] key and hit [enter] to select the debug level - failsafe - ------------------------------------------------------ Cannot enter failsafe mode: Disabled on this system !! ------------------------------------------------------ Please press Enter to activate this console. (none) login: f Password:
- Accounts are still missing
Firmware
- Seems to be encrypted
Firmware Head
0000000: 4253 4230 3032 0002 004e fcc9 6272 6964 BSB002...N..brid 0000010: 6765 0000 0000 0000 0000 0000 0000 0000 ge.............. 0000020: 0000 004e fab0 0103 0000 0000 3031 3033 ...N........0103 0000030: 3032 3632 0000 0000 0000 0000 4bb1 3918 0262........K.9. 0000040: a7ac d534 6aab 63fc cb81 3643 1f9b 53bd ...4j.c...6C..S. 0000050: d9b5 a76d f5bf 82dc 8265 eebc 75d8 5e42 ...m.....e..u.^B 0000060: dbc1 f384 c368 24c3 1988 f97e 9ab3 34c7 .....h$....~..4.
Public key from the end of firmware file
openssl rsa -pubin -text -in a
Public-Key: (2048 bit)
Modulus:
00:a1:ba:a2:33:57:01:4a:be:ba:87:db:5a:c9:c4:
4d:a4:2e:e1:2b:31:48:53:26:2d:4a:2b:65:19:ce:
94:01:2e:0e:81:ff:d9:39:c0:e1:17:09:2d:d1:fc:
e7:89:11:3c:44:48:c4:19:72:be:b5:a2:72:72:1c:
f8:80:e4:f7:05:3d:0e:b0:8f:6d:5a:62:f4:6c:6c:
e3:bf:b7:45:37:64:e5:14:c7:e5:87:55:1a:55:f8:
53:af:3f:b2:11:47:38:56:7a:2d:4b:30:e9:b6:bf:
23:d9:33:3c:08:71:bc:98:ae:3d:0b:92:d8:c4:9f:
d9:42:1d:5d:5e:97:e6:88:74:1b:f9:14:0e:88:af:
fc:83:d4:21:01:c4:86:fd:a3:55:bd:e5:fd:a2:69:
76:d1:c0:e0:2d:0a:f0:e8:20:b9:10:ef:62:33:04:
03:e5:43:13:d1:df:46:6e:eb:df:3c:c4:a2:cb:9c:
48:32:13:1c:85:2e:d9:5c:50:fa:56:99:3a:03:ad:
7a:9b:96:79:57:76:a1:cc:87:a6:9a:d3:04:26:70:
0f:85:b9:2b:48:67:17:bd:b9:3b:e0:c8:10:dc:2b:
83:d8:58:0b:7c:e8:e3:28:a7:c4:e2:17:96:62:7e:
15:0f:ec:cc:8c:6e:ed:40:23:38:dd:a9:5b:a7:31:
7b:15
Exponent: 65537 (0x10001)
writing RSA key
-----BEGIN PUBLIC KEY-----
MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAobqiM1cBSr66h9taycRN
pC7hKzFIUyYtSitlGc6UAS4Ogf/ZOcDhFwkt0fzniRE8REjEGXK+taJychz4gOT3
BT0OsI9tWmL0bGzjv7dFN2TlFMflh1UaVfhTrz+yEUc4VnotSzDptr8j2TM8CHG8
mK49C5LYxJ/ZQh1dXpfmiHQb+RQOiK/8g9QhAcSG/aNVveX9oml20cDgLQrw6CC5
EO9iMwQD5UMT0d9GbuvfPMSiy5xIMhMchS7ZXFD6Vpk6A616m5Z5V3ahzIemmtME
JnAPhbkrSGcXvbk74MgQ3CuD2FgLfOjjKKfE4heWYn4VD+zMjG7tQCM43albpzF7
FQIDAQAB
-----END PUBLIC KEY-----
Attachments
Normal Sort Sort + uniq Sort + uniq + count
WEB-server
$ curl -v '10.0.2.58/description.xml' * Trying 10.0.2.58... * Connected to 10.0.2.58 (10.0.2.58) port 80 (#0) > GET /description.xml HTTP/1.1 > Host: 10.0.2.58 > User-Agent: curl/7.43.0 > Accept: */* > < HTTP/1.1 200 OK < Content-type: text/xml < Connection: Keep-Alive * no chunk, no close, no size. Assume close to signal end < <?xml version="1.0" encoding="UTF-8" ?> <root xmlns="urn:schemas-upnp-org:device-1-0"> <specVersion> <major>1</major> <minor>0</minor> </specVersion> <URLBase>http://10.0.2.58:80/</URLBase> <device> <deviceType>urn:schemas-upnp-org:device:Basic:1</deviceType> <friendlyName>Philips hue (10.0.2.58)</friendlyName> <manufacturer>Royal Philips Electronics</manufacturer> <manufacturerURL>http://www.philips.com</manufacturerURL> <modelDescription>Philips hue Personal Wireless Lighting</modelDescription> <modelName>Philips hue bridge 2015</modelName> <modelNumber>BSB002</modelNumber> <modelURL>http://www.meethue.com</modelURL> <serialNumber>001788xxxxx</serialNumber> <UDN>uuid:2f402f80-da50-11e1-9b23-001788xxxxx</UDN> <presentationURL>index.html</presentationURL> <iconList> <icon> <mimetype>image/png</mimetype> <height>48</height> <width>48</width> <depth>24</depth> <url>hue_logo_0.png</url> </icon> <icon> <mimetype>image/png</mimetype> <height>120</height> <width>120</width> <depth>24</depth> <url>hue_logo_3.png</url> </icon> </iconList> </device> </root>
Landing page (2015-12-30): hue-personal-wireless-lighting.pdf
HW
- CPU: qca4531-bl3a
Memory: https://www.winbond.com/resource-files/da00-w9751g6kbg1.pdf
USB to Serial Bridge Conroller: http://prolificusa.com/files/DS_PL2303SA_d20120504.pdf